What is cyberwar? What is cybercrime? This quick post explains the differences.
 Photo by Stilness InMotion on Unsplash
Photo by Stilness InMotion on Unsplash
Cyberwar
Cyberwar is an act of aggression carried out by or on behalf of state-based actors in cyberspace. The actual threshold of when a cyberattack amounts to cyberwar is debated among academic scholars. At one end of the spectrum, Rid (2012) argues that only cyberwar, which leads to kinetic (physical) effects, such as loss of life or injury, is cyberwarfare, and anything less is cyber-sabotage, cyber-espionage or cyber-subversion. Whilst Stone (2013) argues that cyberwar is more broadly defined to include acts of aggression such as cyber-sabotage, that is, activities that lead to the destruction of property or the disruption of services. For the attack to be cyberwar, it must be an action by one state on another that intends to render its opponent defenceless or force them to submit to the attacker. An example of cyberwar is the Stuxnet virus, which in 2005 sabotaged Iran’s nuclear enrichment program. The Equation Group created the virus (linked to the United States NSA) and was likely a joint operation with Israel. The virus modified firmware on SCADA system centrifuges which destroyed them (Langner, 2011).
Cybercrime
Cybercrime, in broad terms, is defined as “any crime that is facilitated or committed using a computer, network, or hardware device” (Gordon & Ford, 2006, p. 14). Cybercrimes, much like real crimes, have perpetrators and victims. Cybercrimes are on a continuum of sophistication in their technology usage, ranging from “technology-centric crimes” to “people-centric crimes”. A recent example of a technology-centric crime is the Colonial Pipeline attack where hackers broke into networks using compromised credentials, then deployed ransomware onto the network crippling the company’s infrastructure. This would be on the left of the continuum (see Figure 1). The crime involved high levels of technology such as hacking and custom code. At the other end of the spectrum, people-centric crimes are regular crimes committed with the use of technology, such as harassment, stalking, and dissemination of child pornography. These are crimes where computer software and tools used by everyone can be used to commit a crime.
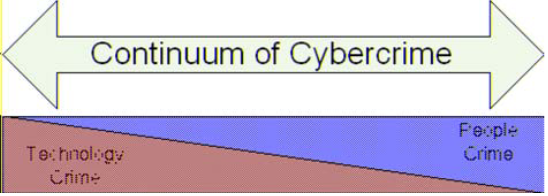
Figure 1 - The Continuum of Cybercrime (Gordon & Ford, 2006, p. 15)